It’s expensive and time-consuming but necessary ensuring the security and privacy of customer data is paramount. One effective way organizations demonstrate their commitment to data security is by obtaining a SOC 2 report. We provide finance and accounting teams with a deeper understanding of SOC 2 reports, their importance, and the role they play in facilitating the process.
Understanding SOC 2 Reports: A SOC 2 report is an independent attestation by a certified public accountant (CPA) that evaluates an organization’s internal controls related to security, availability, processing integrity, confidentiality, and privacy. These reports are based on the AICPA’s Trust Services Criteria, which define the trustworthiness of an organization’s systems and processes.
https://us.aicpa.org/interestareas/frc/assuranceadvisoryservices/aicpasoc2report
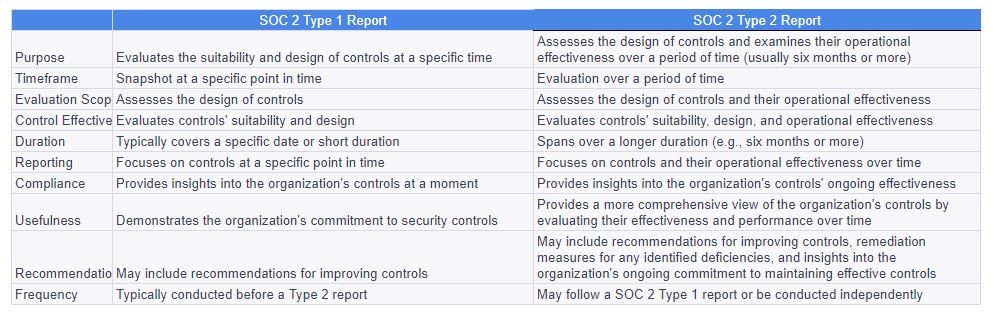
Types of SOC 2 Reports: There are two types of SOC 2 reports:
SOC 2 Type I Report:
- Evaluates the suitability and design of an organization’s controls at a specific point in time.
- Provides a snapshot assessment of controls at a particular moment.
SOC 2 Type II Report:
- Assesses the design of controls and examines their operational effectiveness over a period of time, usually six months or more.
- Offers insights into the ongoing effectiveness of controls and their performance over time.
Examples of SOC 2 Reports:
SOC 2 reports can cover various aspects of an organization’s operations on security and safeguards to include:
Security:
- Focuses on the effectiveness of security measures to protect sensitive data from unauthorized access, both physical and logical.
Availability:
- Assesses the organization’s ability to ensure that its systems and services are accessible and operational as agreed upon with customers.
Processing Integrity:
Evaluates the accuracy, completeness, and timeliness of processing transactions and data.
Confidentiality:
- Examines the measures taken to safeguard confidential information and prevent unauthorized disclosure.
Privacy:
- Assesses the organization’s practices in collecting, using, retaining, and disclosing personal information in compliance with applicable privacy laws and regulations.
- IV. Failing a SOC 2 Audit: Yikes, failing a SOC 2 audit can have significant repercussions for an organization, including:
Loss of Trust and Reputation:
- Raises concerns about the organization’s ability to adequately protect customer data, leading to a loss of trust from existing and potential clients, partners, and stakeholders. Customers and Vendors are requiring it more and more these days.
- Damaged reputation may result in customer attrition, decreased business opportunities, and a negative impact on the organization’s brand image.
Legal and Regulatory Consequences:
- Depending on the industry and the nature of the data involved, failing a SOC 2 audit may have legal which is costly.
- Non-compliance with industry-specific regulations or privacy laws can result in fines, penalties, or legal actions brought against the organization.
Increased Security Risks:
- Failing a SOC 2 audit signifies that the organization’s controls and security measures are insufficient or ineffective so once again reputation risk.
- This leaves the organization vulnerable to security breaches, data theft, or unauthorized access to sensitive information, attracting the attention of malicious actors.
Business Disruptions and Financial Losses:
- Failing a SOC 2 audit often requires the organization to invest time and resources in addressing identified control deficiencies and remediating the issues.
- This can lead to business disruptions and additional costs associated with implementing new controls, conducting additional audits, or engaging external consultants.
- Moreover, the loss of clients or business opportunities due to a failed audit can result in financial losses for the organization.
Limited Market Access:
- Many organizations prioritize data security and privacy when selecting partners or entering into contracts.
- Failing a SOC 2 audit may restrict the organization’s ability to form partnerships or engage in business relationships with companies that prioritize stringent data security measures.
Role of Finance and Accounting Team Members in SOC 2 Compliance:
Finance and accounting teams play a crucial role in supporting SOC 2 compliance efforts. Here are key areas where they can help:
Documenting Controls:
- Collaborate with IT and relevant departments to identify and document controls that impact the Trust Services Criteria.
- Examples include controls related to financial data access and authorization, segregation of duties in financial processes, and data encryption protocols for financial systems. You only want the right people to access the systems and you don’t want all your passwords on a Google Sheet.
Aligning Policies and Procedures:
- Ensure that the department’s policies and procedures align with the security and privacy requirements defined in the Trust Services Criteria.
- Review and update policies related to data retention, financial reporting, and vendor management to ensure compliance with the criteria. We try to do this across the departments with a template.
Conducting Risk Assessments:
- Work closely with IT and internal audit teams to identify and assess potential risks to financial and accounting systems, processes, and data.
- Perform risk assessments to evaluate the potential impact of unauthorized access to financial systems or the loss of critical financial data.
Monitoring Compliance:
- Play a vital role in monitoring and documenting compliance with established controls and procedures.
- Regularly review and reconcile financial transactions, analyze access logs for financial systems, and perform periodic audits to provide evidence of ongoing control effectiveness.
Assisting in Remediation:
- Work with IT and other teams to address control gaps or deficiencies identified during the SOC 2 assessment.
- Actively participate in the implementation of remediation measures, such as stronger authentication mechanisms for financial system access or enhanced data backup and recovery procedures.
Also talk to a consultant as needed. Oftentimes we contact our friends at Phoenix when we have questions. https://phoenixadvisorygroup.io/
Finance and accounting teams can contribute to strengthening data security, maintaining compliance, and protecting the organization’s reputation. The AICPA after all, is a finance authority and Finance can take the lead in getting a SOC 2 report done.